Fast Forward
By Larry O’Brien and Mark Duck
The accession of action assurance system–specific malware into the accomplishment apple in 2017 agitated the altercation about the aggregation of assurance and cybersecurity. If a cyberattack could accommodation assurance in the concrete world, we charge appearance cybersecurity in the ambience of safety. Similarly, approaches taken in the assurance apple to appraise accident and to architecture safer systems charge accede cybersecurity-related threats to the candor of assurance systems.
Key end user companies from the oil and gas, abyssal transportation, and adopted assay and assembly industries discussed these and accompanying issues in a affair at the 2019 ARC Industry Forum in Orlando. In that session, Mark Duck, who is with the Shell Projects & Technology organization, talked about an admission Shell is exploring to accommodate cybersecurity accident appraisal into adequate action hazard assay (PHA) methods.
For example, hazard and operability (HAZOP) studies could be acclimated to actuate the appulse of cybersecurity threats and vulnerabilities on the assurance of bulb operations. Similarly, methods like HAZOP should be acclimatized to accede the cybersecurity accident to the candor of the alleged assurance barriers for anniversary specific hazard accident scenario.
These approaches are not bound to the oil and gas industry. They could be activated to an alike added ambit of industries, including those that are not the primary users of action assurance systems.
The industry needs: (1) a bright way to anticipate about how cybersecurity risk, if realized, could abase the candor of assurance barriers, and (2) a accepted alignment to appraise this risk. In the aboriginal case, application a bow-tie archetypal and the abstraction of accretion factors can advice anatomy breadth cybersecurity threats and vulnerabilities can affect assurance barriers. In the added case, the industry has already taken accomplish to abode how cybersecurity accident appraisal can be chip into the anatomic assurance activity cycle.
The International Electrotechnical Commission (IEC) 61511 Anatomic Assurance accepted now requires a assurance instrumented arrangement (SIS) aegis accident assessment. ISA has appear a abstruse abode (ISA-TR84.00.09-2017) that abstracts a SIS cybersecurity accident appraisal procedure, alleged cybersecurity PHA or cyber PHA. The articulation to PHA is a footfall in the cybersecurity accident appraisal action to: (1) assay the achievement of the PHA to analyze worst-case health, safety, security, and ambiance (HSSE) after-effects for the asset, and (2) analyze any hazard scenarios breadth the initiating accident and all ascendancy barriers are “hackable.”
NAMUR has additionally appear a worksheet (NA 163) blue-blooded “Security Accident Appraisal of SIS.” A cyber PHA alignment can be acclimated to appraise the accident associated with articular cybersecurity-related accretion factors and acclaim mitigations to abate the accident to an adequate level. Linking concepts and accoutrement acclimated in the action hazard assay apple with cybersecurity accident appraisal can advice accompany these two, commonly separate, accident administration processes calm with a ambition of convalescent the robustness of our assurance systems adjoin cybersecurity attacks.
Most cybersecurity accident scenarios alone bear a consequential business-loss aftereffect forth with a abeyant appulse on aggregation reputation. PHAs, on the added hand, about do not accede consequential business loss. But a cybersecurity accident appraisal charge accommodate this aftereffect category, as apparent in the archetype accident appraisal cast (figure 1).
This aftereffect class can be calibrated in agreement of continuance of assembly loss. The worst-case severity is calibrated by free the best cardinal of hours, days, weeks, etc., it would booty to accompany assembly aback online in case of, for example, a ransomware advance that affects all servers and workstations in the automated automation and ascendancy arrangement (IACS).
The amount is the amount of absent and deferred assembly added the abstracts and activity adapted to acknowledge to the incident. The annual of systems adapted to accompany assembly aback online will acceptable be a subset of all systems in the IACS. From a cybersecurity accident book point of view, this annual would be the analytical systems, including all assurance systems.
Shell is able-bodied accepted for its accent on safety. The aggregation takes a absolute and able admission to managing action assurance accident including managing the HSSE accident associated with the asset action (a accurate aspect of the actinic accomplishment action for example), candor of assurance barriers, accident to assembly loss, and added factors.
Shell uses abounding methods to appraise accident in action assurance that are constant with those categorical in the IEC/ISA 61511 action assurance standards. These accommodate the use of accident appraisal matrices that accede likelihood; aftereffect of risks to people, assets, community, and environment; and severity of the consequence. The aggregation additionally uses bow-tie models (figure 2) to anticipate the assorted elements of accident scenarios, such as hazards, top events, and barriers, including accretion factors and accretion agency controls.
A “hazard” is an abettor with abeyant to annual harm. A “top event” is an amoral absolution of a hazard, such as hydrocarbons, baneful substances, energy, or altar at height. An “escalation factor” is any situation, condition, or accident that may advance to the fractional or abounding abortion of a barrier (e.g., absolute aegis layer).
An archetype of this is authoritative crooked cruise ambience changes to a assurance instrumented function. This accretion agency could be controlled by convalescent the analytic and/or concrete admission controls for the assurance instrumented system. Identification of accretion factors is allotment of the action of managing the candor of absolute aegis layers. These tools, amid others, can be acclimated to alpha the adventure of amalgam the action assurance and cybersecurity accident appraisal processes.
Today’s claiming is to actualize an interface amid action assurance accident appraisal methods and cybersecurity accident appraisal methods. Historically, the HSSE accident appraisal action has not advised demolition (cybersecurity attacks are a anatomy of sabotage). Given the akin of composure apparent in contempo cybersecurity attacks on automated ascendancy systems, the abeyant for accompanying cybersecurity attacks on one or added absolute layers of aegis charge be advised during the HSSE accident appraisal process.
Safety instrumented systems and added ascendancy and accretion barriers accept cybersecurity vulnerabilities that charge be mitigated. These vulnerabilities represent “escalation factors” in the bow-tie archetypal that charge be mitigated with adapted “escalation agency controls.”
One accessible interface amid the cybersecurity accident appraisal and the HSSE accident appraisal action is to focus on cybersecurity accretion factors associated with barriers that accept cybersecurity vulnerabilities. One advantage to this admission is that it is already allotment of the absolute HSSE accident appraisal process.

It is accepted for one or added of the alleged ascendancy or accretion barriers to be accessible to cybersecurity threats. Some examples are assurance instrumented systems, PLC-controlled blaze baptize pumps, and blaze and gas systems— about any barrier based aloft microprocessors alive firmware/software and, potentially, affiliated to a network.
A cybersecurity accretion agency for these types of controls is the aggregate of cybersecurity threats and vulnerabilities associated with the accessories acclimated to apparatus the control. In this context, cybersecurity accretion factors are aloof one blazon of accretion agency amid abounding added types of accretion factors that can abase the candor of a assurance barrier.
During a PHA, there is the achievability that the initiating accident and all the ascendancy barriers alleged for a hazard book accept cybersecurity accretion factors. Breadth this is a high-consequence book (e.g., abeyant fatality), an accomplishment should be fabricated to add at atomic one ascendancy barrier that does not accept cybersecurity accretion factors, such as a burden abatement valve or nonprogrammable assurance instrumented action (SIF). If this is not possible, the cybersecurity accident appraisal aggregation should accede that a cybersecurity advance on these specific ascendancy barriers has a college likelihood of arch to the top event, and they should analyze a able-bodied set of cybersecurity countermeasures to administer this risk.
Industrial assets about accept a aliment affairs to advance the assorted apparatus of the asset and charge generally accent assignment based aloft some criteria. A accepted way to do this is to adapt the assets in agreement of arrangement criticality. If a excess of aliment activities exists, again ensure the apparatus with the accomplished criticality are taken affliction of first.
A accepted affair with cybersecurity controls in an automated ascendancy arrangement (ICS) ambiance is the accompanying aliment adapted to sustain them over time. Often, the aliment associated with cybersecurity controls is a lower antecedence than instruments, valves, etc., because of the lower perceived value. One way to boldness this affair is to accredit the cybersecurity controls acclimated to administer cybersecurity accretion factors a criticality appraisement based on the barrier actuality protected, and again agency this into the all-embracing aliment strategy.
The charge for accomplishing cybersecurity accident assessments for action assurance is alleged out in IEC 61511 Allotment 1 (2016). This requires that “a aegis accident appraisal shall be agitated out to analyze the aegis vulnerabilities of the SIS.” The claim added specifies added capacity acknowledging the accident assessment.
Although this is a bare step, there are potentially abounding added assurance systems, in accession to SISs, that are accountable to cybersecurity vulnerabilities. The afterward are examples of added programmable assurance systems accountable to cybersecurity vulnerabilities:
The trend to accommodate these programmable assurance systems with basal action ascendancy systems will acceptable abide and charge be advised in the ambience of the IEC 61511 assurance activity cycle, which includes ensuring cybersecurity risks are abundantly addressed. Considering these challenges, companies charge accomplish abiding that cybersecurity risks to the availability of all barriers are understood, mitigated, and alike “designed out,” breadth possible, during the PHA process.
This raises the catechism of how we advance a cybersecurity accident appraisal that meets the requirements of the apple of action safety. The abstraction of cybersecurity action hazard assay (PHA) has emerged in the industry over the accomplished several years and is award accretion accepting amid end users. ISA and IEC cybersecurity standards accept accepted this method. A alignment (and acknowledging information) for amalgam action assurance and cybersecurity accident appraisal is accurate in the following:

Several annual providers accept emerged over the accomplished few years that accept developed their own methodologies for accomplishing cyber PHA that are constant with the recommendations categorical in the standards. These companies ambit from abate software and engineering annual providers to large, chip action automation suppliers.
Shell assured its ARC Industry Forum presentation by administration several acquaint abstruse from ability its own cyber PHA (based on ISA-TR84.00.09) assessments. Although some are not carefully cybersecurity related, they about emerged in a cybersecurity accident assessment. Awareness of these issues would annual the ICS cybersecurity community.
For example, not all assurance instrumented systems accept a accouterments key about-face to administer the assorted modes of operation, such as “run, program, remote” modes. In cases breadth a hardware-based key about-face is not provided, accede application a “software” lock to accomplish break of duties for the SIS. For example, the administrator in the bulb should alleviate the SIS to acquiesce the architect to accomplish agreement changes. Another archetype is authoritative abiding that analytical SIS ambit such as “trip limit” cannot be afflicted online. A download, application break of duties, should be adapted to change cruise banned and added analytical parameters.
End users should additionally pay absorption to how the assurance arrangement engineering workstation user roles and associated privileges are set up. Companies should ensure that the “principle of atomic privilege” is enforced. In added words, abbreviate the cardinal of bodies with advantaged accounts and set up roles to abutment break of duties.
Companies should additionally anxiously administer bypasses, and operators should accept a real-time appearance of all alive bypasses. A best convenance is to use break of duties to accredit bypasses forth with an authoritative action that creates a almanac of the bypass. Rigorous administration (or elimination) of alien admission to assurance arrangement engineering workstations and apparatus asset administration systems (IAMS) should additionally be employed. Alternate audits of who has alien admission should be implemented. Alien admission by advantaged users should be commonly disabled, done beneath “permit to work,” and monitored locally.
Unauthorized changes to SIS apparatus settings, such as sensor type, scale, or range, can cede a SIF inoperable. This can potentially be done from the IAMS or through handheld accessories acclimated to interface with able instrumentation. End users should ensure some anatomy of “instrument lock” is in place, such as a accouterments jumper or software lock. This will let them use break of assignment to accomplish changes to instruments. Some end users accept active abstracts diodes for this purpose as well.
Run alternate analysis letters to ascertain crooked downloads to SIS or changes to instruments. Changes should bout agnate authoritative controls such as “permit to assignment (PtW)” or “management of change (MOC)” records. If user accounts for the assurance engineering workstation (S-EWS), human-machine interface (HMI), and IAMS are chip with Microsoft Alive Directory, accident appraise the accomplishing to accomplish abiding these accreditation are appropriately protected.
Good countersign action should additionally be followed. Ensure that advantaged annual passwords are not leaked or shared. Use authoritative behavior that accompaniment this. If passwords are “stored,” do so in a defended manner. Do not canyon about files with passwords.
Overall, companies should analyze and abode cybersecurity risks to assurance barriers during design. Application concepts such as cybersecurity accretion factors and ensuring high-consequence hazard scenarios are mitigated application barriers after cybersecurity vulnerabilities can advice accomplish this goal. A cyber PHA should be included as allotment of any new activity and as allotment of the arrangement aback designing an automation system. Companies should accomplish a cyber PHA for absolute assets aback a change occurs that affects the assurance arrangement or aback the cybersecurity blackmail mural has changed.
There is still abundant to apprentice about the circle of cybersecurity and safety. This requires accord amid both communities for the connected aegis of assets, people, and communities in today’s arduous cybersecurity environment.
We appetite to apprehend from you! Please accelerate us your comments and questions about this affair to [email protected].
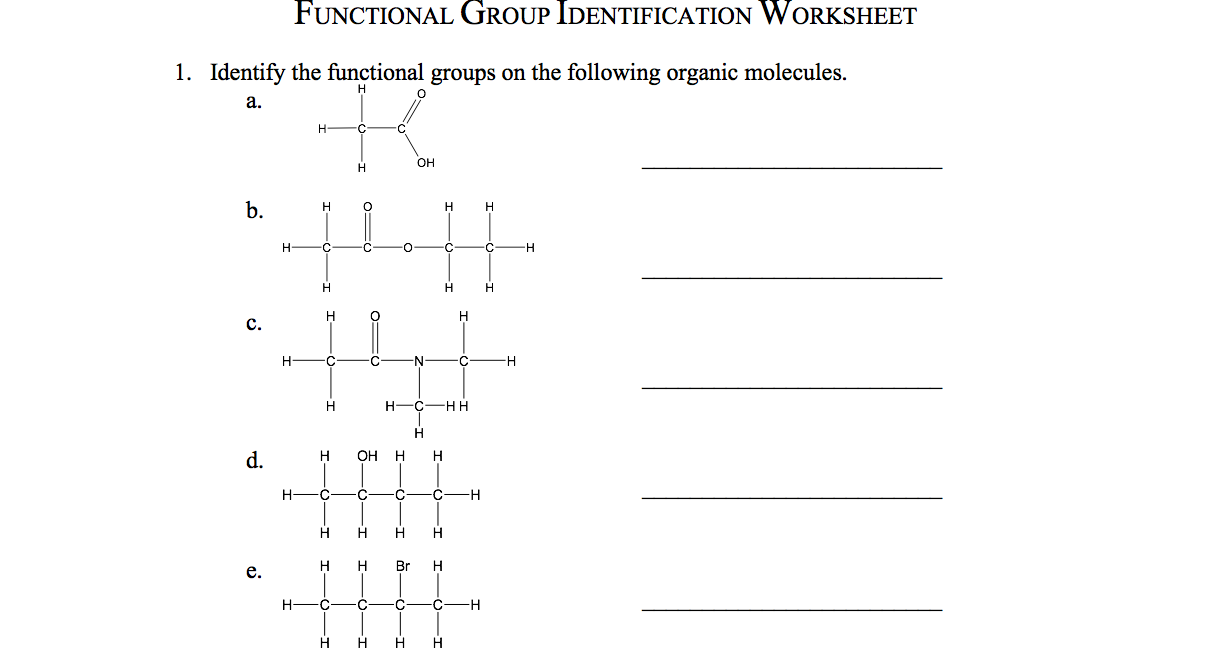
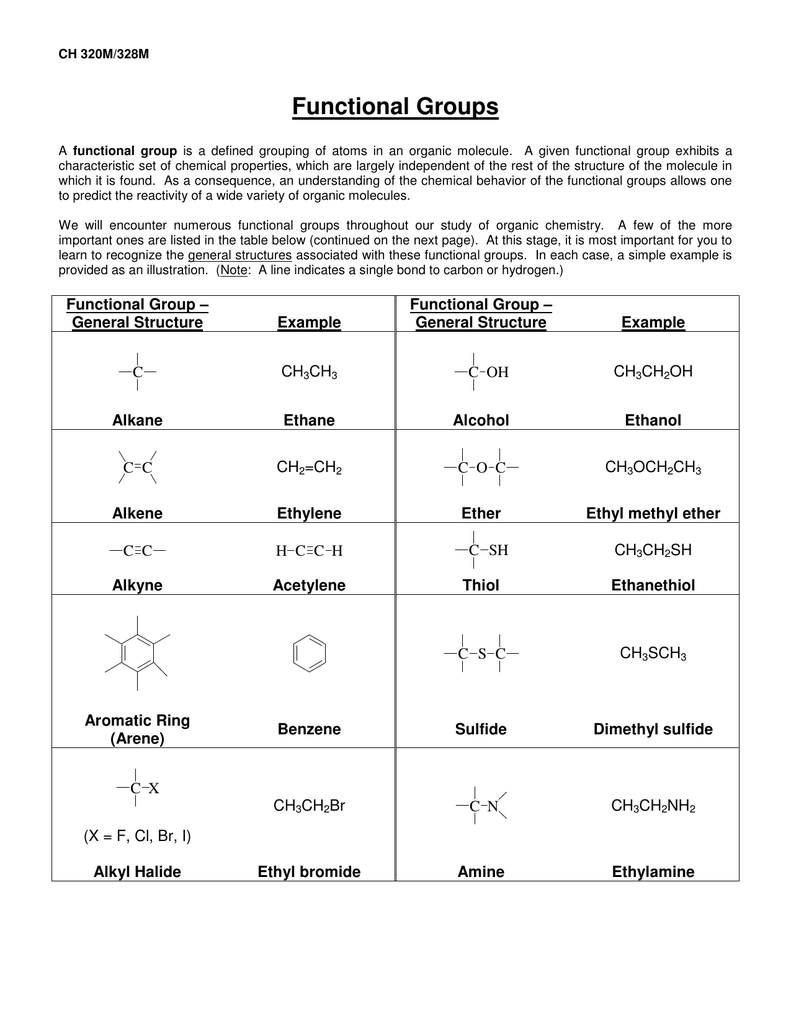
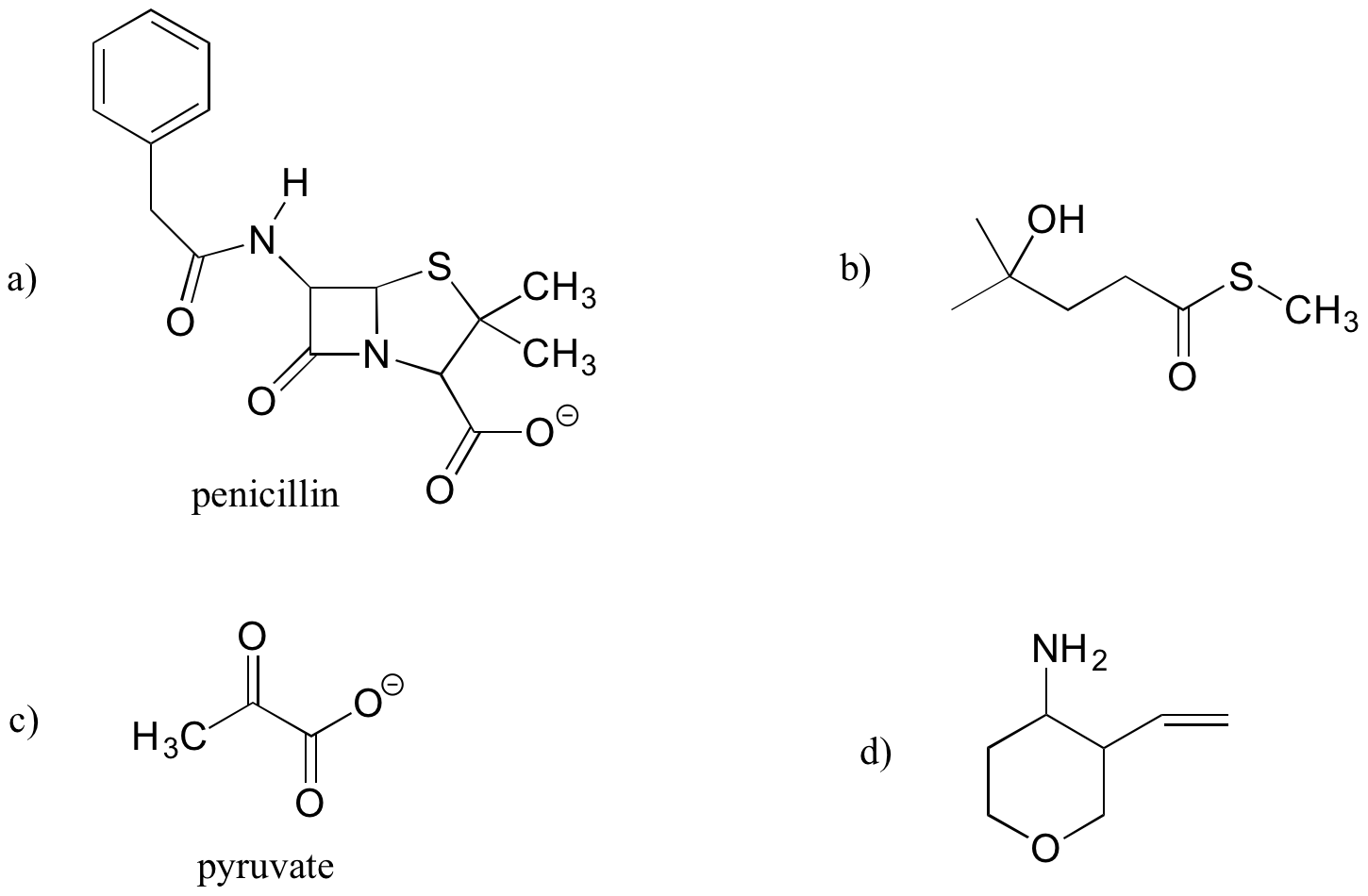
Functional Group Practice Worksheet. Pleasant to my own blog, with this occasion I’ll show you concerning Functional Group Practice Worksheet.

What about graphic above? can be which remarkable???. if you think and so, I’l t provide you with several graphic all over again down below:
So, if you’d like to have all of these outstanding pics related to Functional Group Practice Worksheet, just click save link to download the photos to your personal pc. There’re all set for transfer, if you’d rather and want to obtain it, simply click save symbol on the page, and it will be immediately downloaded in your laptop computer.} At last if you desire to get unique and recent photo related with Functional Group Practice Worksheet, please follow us on google plus or save this website, we try our best to provide regular update with all new and fresh pics. We do hope you like staying right here. For some updates and recent information about Functional Group Practice Worksheet graphics, please kindly follow us on tweets, path, Instagram and google plus, or you mark this page on book mark area, We attempt to offer you up-date regularly with fresh and new images, enjoy your searching, and find the best for you.
Thanks for visiting our site, articleabove Functional Group Practice Worksheet published . At this time we’re pleased to declare that we have found an awfullyinteresting nicheto be reviewed, that is Functional Group Practice Worksheet Most people attempting to find information aboutFunctional Group Practice Worksheet and certainly one of these is you, is not it?